Role Based Access Control
Starting from version 1.5.0, for role-based access control (RBAC), the following functionalities have been added to the floating server:
Two Roles: Admin and User.
Any individual accessing server functionality must be assigned either an Admin or User role.
Admin Permissions:
Add new users and admins.
Add and remove licenses (online, offline, and air-gapped).
Configure license and management API URLs.
Set shared and API keys.
User Permissions (Admins and non-admin users):
Register as a floating user.
Add consumptions.
Access reports.
Check server health.
Borrow licenses.
Change their own password.
This RBAC model applies to both browser and API access.
Start the Server
To start the server in authentication mode, use the following command:
./floating-server -userAuthentication true
API Access
For API access, users must first log in and obtain a JWT, which is then included in subsequent requests. An example is shown below.
If a user attempts to register without logging in, they will receive an error prompting them to log in first.
Response:
{"message":"Unauthorized: Please log in"}
To log in, users send a request containing their username and password to the /auth endpoint. An example is shown below.
Response:
{"message":"Login successful","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJyb2xlIjoidXNlciIsInVzZXJuYW1lIjoidXNlcjEifQ.laskPwD_z36WjODEGKNpVojnouqXYCtKr9HXrLPBqWw"}
This endpoint returns a JWT, which the user must then include in subsequent requests. After receiving the token, the user can resend the registration request using the JWT for authentication.
The registration is successful.
Browser
The login page in authentication mode:
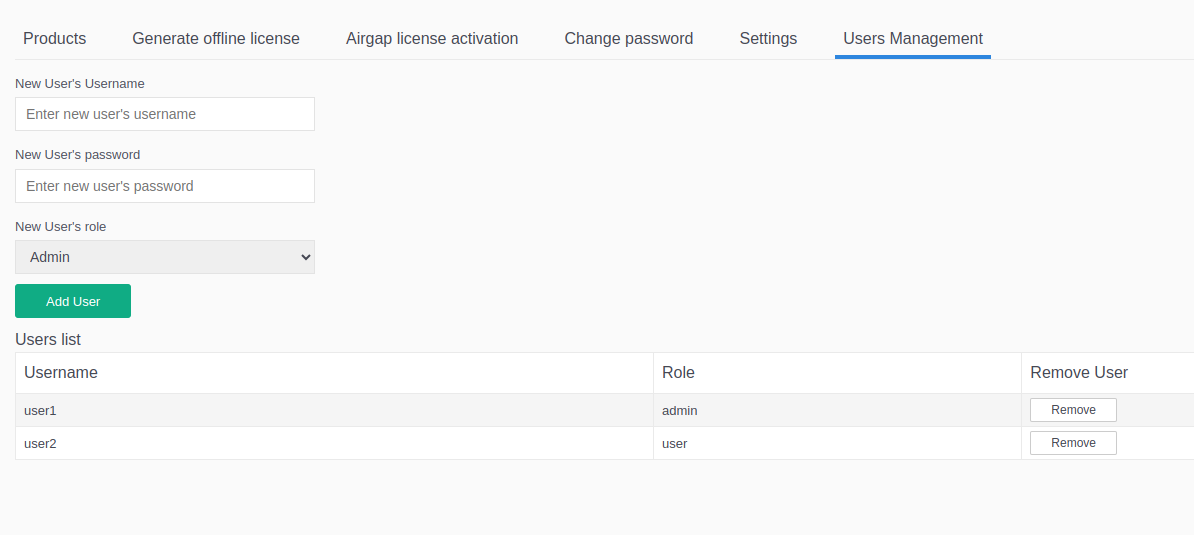
The Users Management tab displays a list of all users and their assigned roles.
Admin Permissions:
Admins can add new users or remove existing ones.
When adding a user, the admin assigns a temporary password, which the user must change upon their first login.
Users and admins can change their own password from the Change password tab:
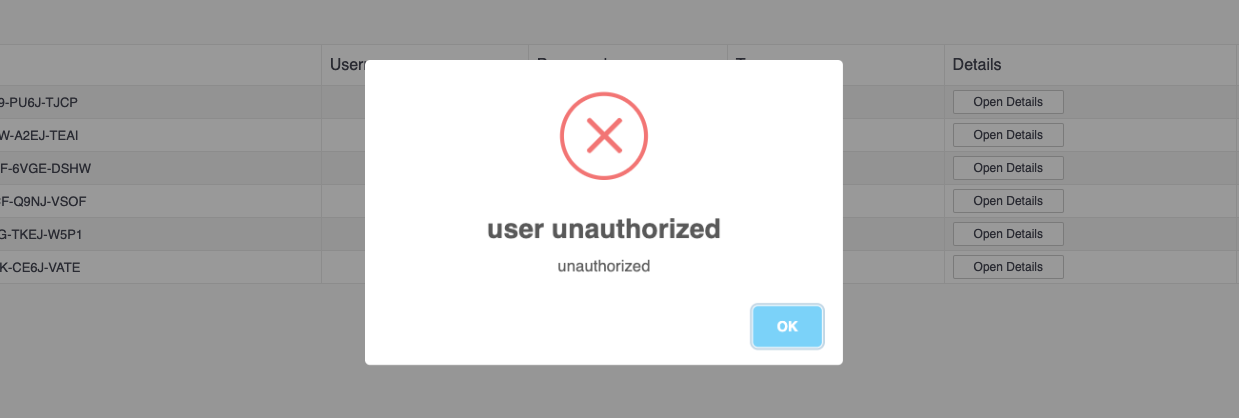
If a non-admin user attempts to perform actions restricted to admins, they will receive an error message, as shown below.
Initialize Users
Initializing the First Admin User
Example YAML format for admin setup:
Note on version 1.5.0 vs later versions
In version 1.5.0, user initialization in the config file allowed multiple users with any role to be specified. The configuration format for multiple users looked like this:
Starting from version 1.5.1, user initialization is limited to a single admin user at the setup stage.
Number of Admins
At least one admin is required when running the server in authentication mode. If no admin is configured, the server will fail to launch, displaying an error message requesting you to provide the necessary configuration.
Storage
User information is stored in the database, and passwords are securely stored as hashed values.
Was this helpful?