Vendor Platform SSO
The LicenseSpring Vendor Platform supports Single Sign-On (SSO) to allow internal users—such as administrators, developers, and support teams—to securely access the management dashboard using their organization's identity provider (IdP). By integrating SSO, vendors can enforce centralized authentication policies and streamline access control across their team.
This section provides a step-by-step guide to configure SSO within the Vendor Platform. The process includes registering your SSO provider, configuring SAML or OIDC settings, and verifying the connection. Once enabled, users will be able to authenticate via your IdP using their organizational credentials.
Setup Single Sign On
To configure Single Sign-On (SSO) for your organization, you must first navigate to the appropriate section within the LicenseSpring Vendor Platform. This is where you can add and manage your identity provider (IdP) settings.
Follow the steps below to access the SSO configuration view:
Log in to the Vendor Platform
Go to https://saas.licensespring.com and sign in with your admin credentials.
If you do not see the “SSO Settings” tab, ensure that you have the necessary admin privileges or contact your LicenseSpring account manager.
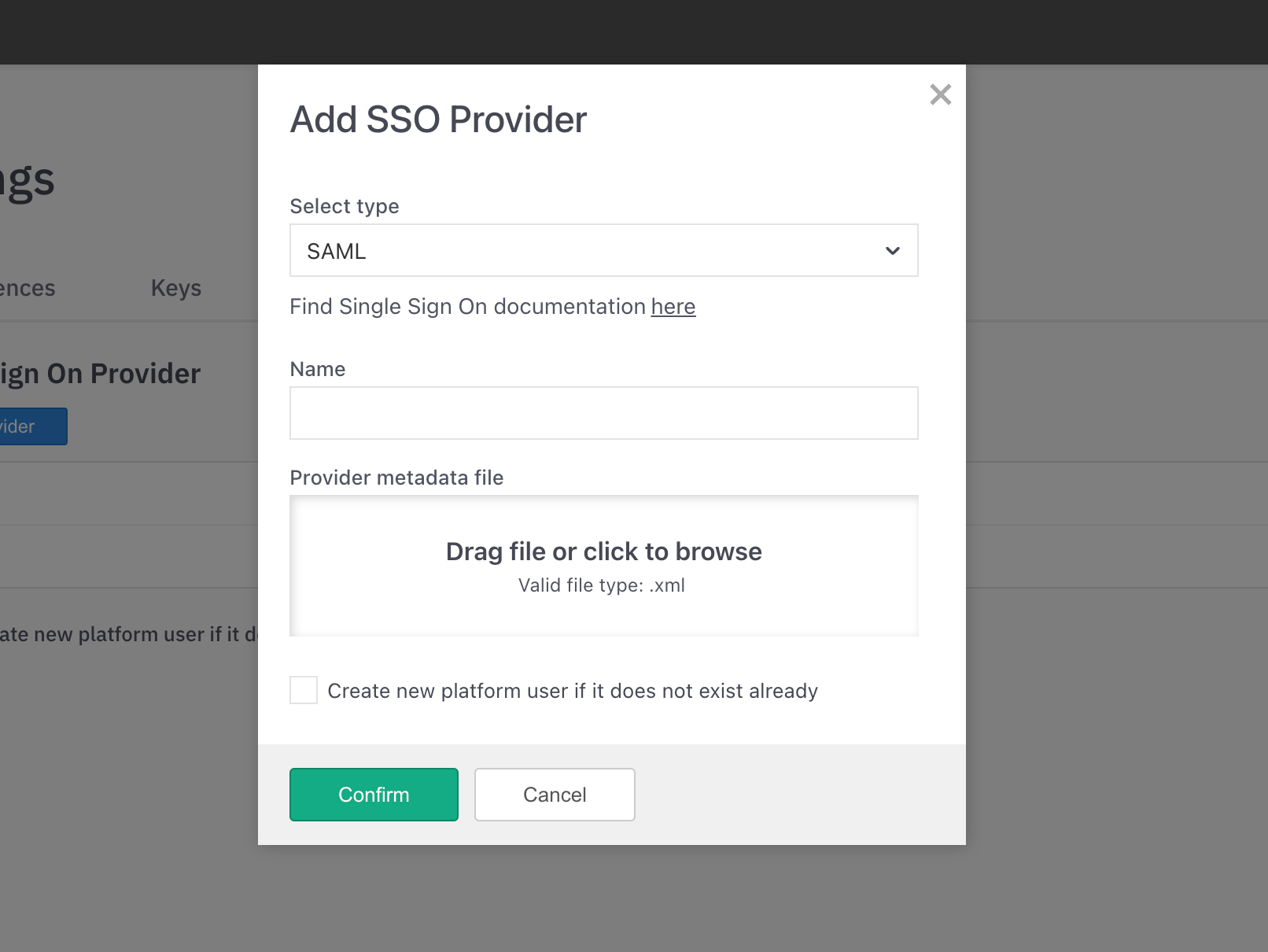
Depending on your selected Identity Provider, you will have to submit the following information:
Nameand.xml provider metadata filefor SAML providers.Name,Client IDandClient secretfor Google identity provider.Service ID,Key ID,Team IDand.p8 key filefor Apple identity provider.
Check Create new platform user if it does not exist already if you want to allow all users from your identity provider to login to the LicenseSpring platform. In that case for every new logged in user, LicenseSpring will create a new vendor application user for your account.
Instructions on how to register your application to acquire required informations are described below.
Extracting the Company Code
You will need the Company code to successfully register your application in your identity provider dashboard. To find your company code, follow the next steps:
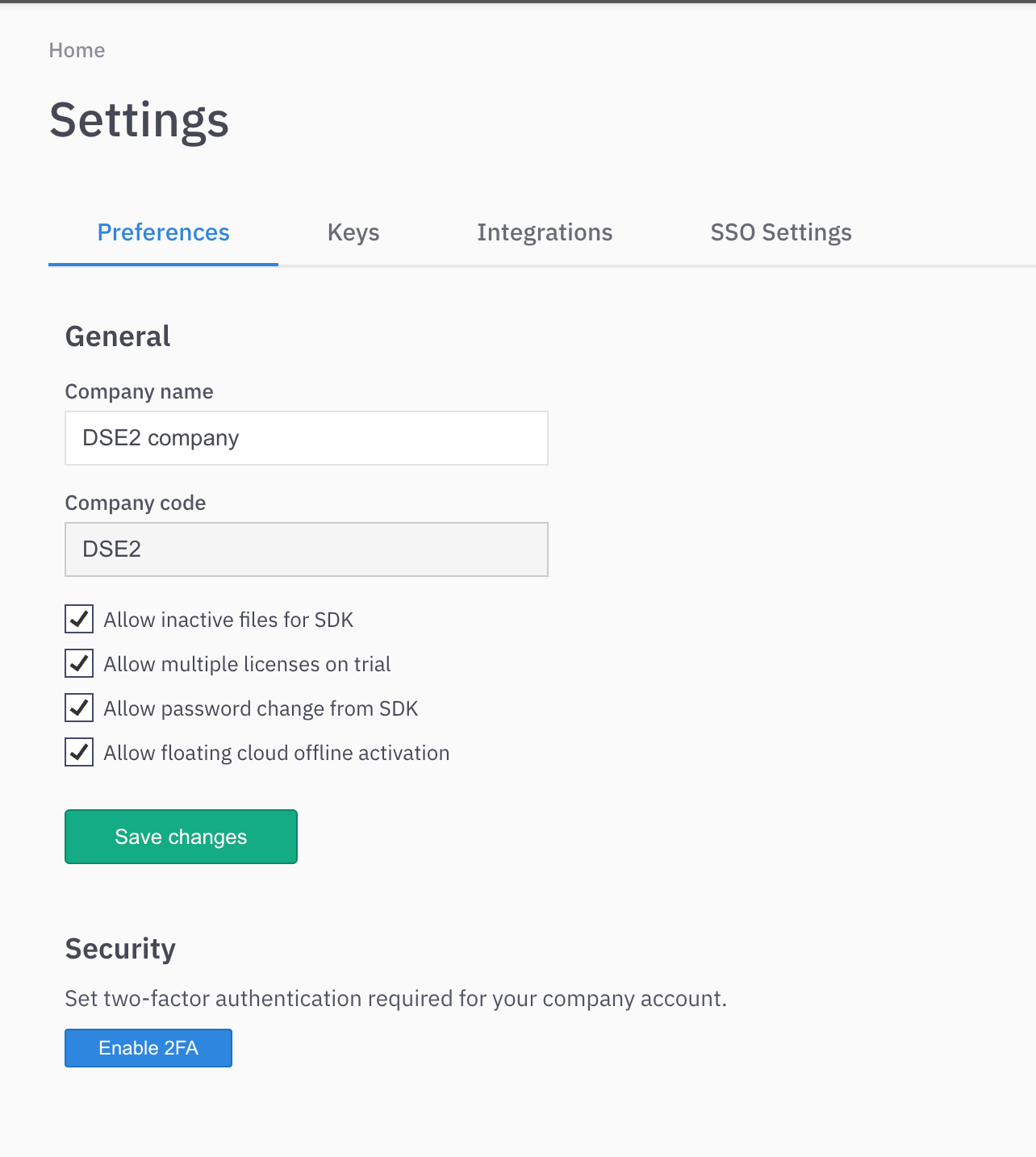
Inside LicenseSpring vendor platform navigate to Settings → Preferences
Pay attention to the Company code field. In this example the Company code is DSE2
Integrating Social Identity Providers
Before setting up a social IdP, it's necessary to register your application with the respective IdP to acquire a client ID and client secret.
Google
Register and configure the consent screen
Create a developer account with Google if you haven't already: https://developers.google.com/identity
Access the OAuth consent screen page: https://console.cloud.google.com/apis/credentials/consent
Opt for the
externalUser Type and proceed to create it.Provide
app information,app domain(optional), anddeveloper contact details.Save and move forward.
Configure Scopes: include
.../auth/userinfo.email,.../auth/userinfo.profile,openid.Update settings and save.
Continue to Test users settings and save.
Create OAuth credentials
Navigate to the Credentials page: https://console.cloud.google.com/apis/credentials
Choose
Create credentials→OAuth client ID.Select
Web applicationtype, name your OAuth 2.0 client.Add URIs:
Authorized JavaScript origins: https://auth.licensespring.com
Authorized redirect URIs: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint (replace {COMPANY_CODE} with your company code)
Create and note down your
Client IDandClient Secret.Go back to the
Add SSO Providerform in the LicenseSpring vendor platform and finish the setup.
Apple
Create Developer Account & App ID
Go to the Apple Developer Console: https://developer.apple.com/account/
If you don't have an Apple Developer account, create one and enroll in the Apple Developer Program.
Navigate to "Certificates, Identifiers & Profiles" → Identifiers → "+" to create a new App ID.
Choose "App IDs", enter a description and a bundle ID (e.g., keycloak).
Under "Capabilities", enable "Sign in with Apple". Register the App ID.
Create a Service ID
Under Identifiers click "+" → select "Service IDs".
Enter a description and an identifier (e.g., keycloak-service). Register it.
Edit the Service ID, enable "Sign in with Apple" and configure the redirect URI: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint
Add the primary App ID created earlier as the Primary App ID and save.
Gather IDs and finish
Note your Team ID from your Apple Developer account.
Note the Key ID from the key details.
Note the Service ID (from step above): keycloak-service.
Have your .p8 key file ready to upload on the platform.
Go back to the
Add SSO Providerform in the LicenseSpring vendor platform and finish the setup.
Incorporating SAML Identity Providers
To enable SAML IdP sign-in for your app users:
Follow your SAML identity provider's instructions to add a relying party or application for your SAML 2.0 IdP.
Configure the assertion consumer endpoint in your SAML identity provider to: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint
Existing legacy configs (DO NOT USE FOR NEW CONFIGS): https://{domain_name}.auth.{region}.amazoncognito.com/saml2/idpresponse
Some SAML IdPs might require the SP urn / Audience URI / SP Entity ID:
Use https://auth.licensespring.com/realms/platform
Existing legacy configs (DO NOT USE FOR NEW CONFIGS): urn:amazon:cognito:sp:{_user_pool_id}
Configure your SAML IdP to provide an email value (claim) in the SAML assertion.
Support SAML 2.0 federation with post-binding endpoints to ensure direct receipt of SAML responses via a user agent.
Go back to
Add SSO Providerform in the LicenseSpring vendor platform and finish the setup.
Microsoft Entra (formerly Azure Active Directory)
Basic setup in Azure
Access https://portal.azure.com/ and choose Azure Active Directory.
Addanenterprise application.Create your own application, input
name, and selectnon-galleryoption.Choose
single sign-on→SAML.Edit Basic SAML Configuration:
Set Identifier as https://auth.licensespring.com/realms/platform
Reply URL: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint
Legacy (DO NOT USE FOR NEW CONFIGS) alternatives are noted in the previous SAML section.
Save and close the settings.
Download Federation Metadata XML.
Go back to
Add SSO Providerform in the LicenseSpring vendor platform and finish the setup.
Allow SP Initiated Login (instructions)
In the LicenseSpring SSO integration (enterprise application) → Properties → Set "Visible to users?" to No.
Create a new enterprise application, input
name, and selectnon-galleryoption.Under Single sign-on select
Linked.Set the
Sign on URLto: https://auth.licensespring.com/realms/platform/protocol/openid-connect/auth?client_id=platform&redirect_uri=https%3A%2F%2Fsaas.licensespring.com&response_type=code&scope=openid&kc_idp_hint={COMPANY_CODE}
Error: A common Azure DB provider SSO error is shown in the screenshot below:
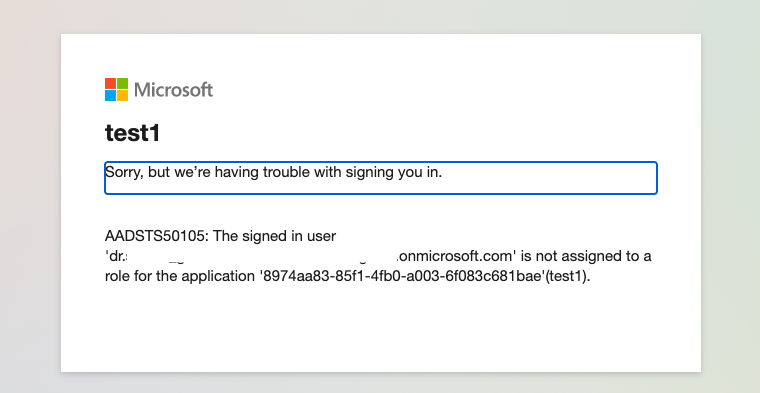
To resolve this error, follow these steps:
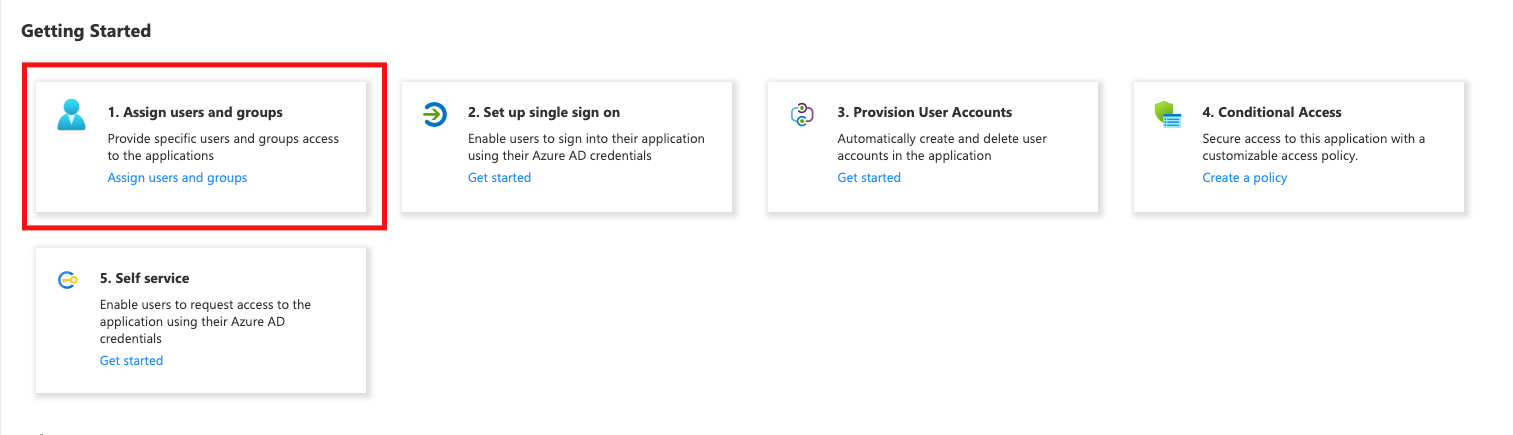
In the Azure Active Directory Admin Center (https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/StartboardApplicationsMenuBlade/AllApps/menuId/AllApps), select your app.
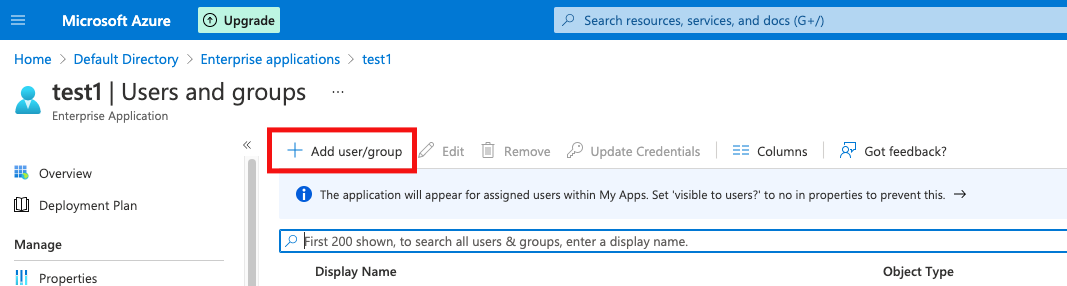
In the left pane select Users and Groups → Add User/Group.
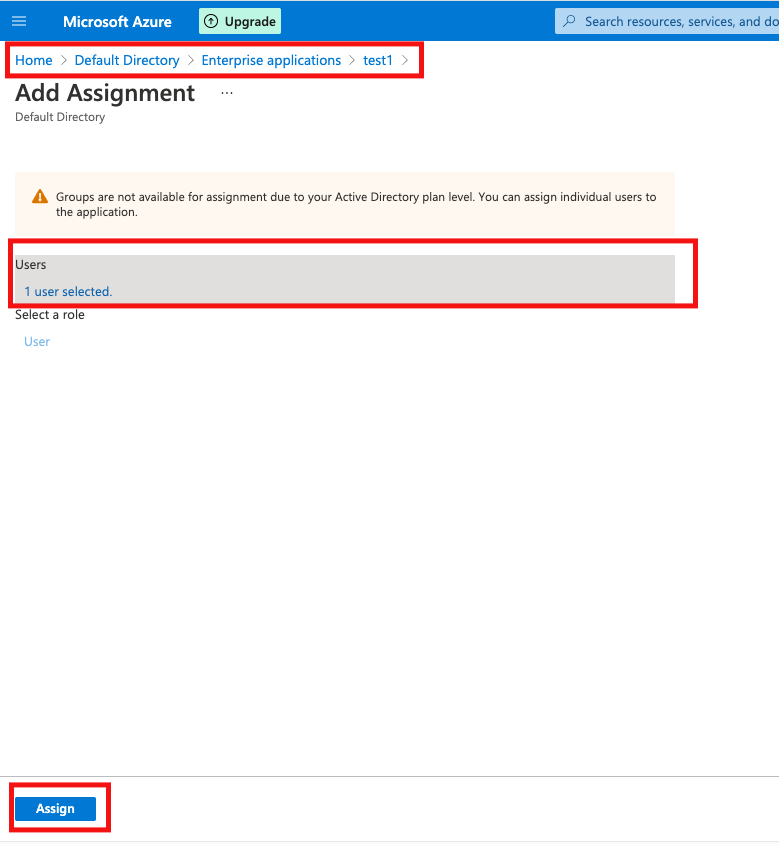
On the Add Assignment pane, select None Selected under Users and Groups.
Search for and select the user that you want to assign to the application, then select Select.
On the Add Assignment pane, select Assign at the bottom.
Once completed, the user can normally sign in using SSO.
Auth0 (SAML)
Configure SAML Settings
Open the application → Addons → enable SAML2 Web App.
In Addon → SAML2 Web App → Settings:
Application Callback URL: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint
Replace {COMPANY_CODE} with your company code.
Under Settings, input the mappings JSON: { "mappings": { "user_id": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", "email": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress", "given_name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname", "family_name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname" }, "nameIdentifierFormat": "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress", "nameIdentifierProbes": [ "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress" ] }
Optionally use Debug and log in as the test user to verify.
Choose Enable, then Save.
Okta (SAML)
Configure SAML Integration
Under General Settings, enter a name for your app.
For Single sign on URL enter: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint
For Audience URI (SP Entity ID) enter: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint
Optionally add ATTRIBUTE STATEMENTS:
Name: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
Value: user.email
Finish the setup and choose Finish.
SP Initiated login (Okta-specific)
For Single sign on URL use: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint/clients/platform-saml
Uncheck "Use this for Recipient URL and Destination URL".
For Recipient URL use: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint
For Destination URL use: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint/clients/platform-saml
For Audience URI (SP Entity ID) use: https://auth.licensespring.com/realms/platform/broker/{COMPANY_CODE}/endpoint/clients/platform-saml
OpenID Connect (OIDC) Integration
LicenseSpring Platform supports Single Sign-On (SSO) via OpenID Connect (OIDC). Customers may integrate any identity provider that supports the standard Authorization Code Flow, including:
Azure Active Directory (Entra ID)
Okta
Auth0
Google Identity
This feature allows organizations to authenticate their users using their own identity system, while LicenseSpring handles user provisioning and access control.
OIDC Redirect URI
Every OIDC provider must be configured to redirect authentication responses to the following URL:
https://auth.licensespring.com/realms/platform/broker/{company_code}/endpoint
Replace {company_code} with the company code assigned to your organization in LicenseSpring. This redirect URI must match exactly in your identity provider configuration.
Google Identity (OIDC)
Steps for Google
Go to https://console.cloud.google.com
APIs & Services → Credentials
Create Credentials → OAuth client ID
Application type: Web Application
Authorized JavaScript origins:
https://auth.licensespring.com
Authorized redirect URI:
https://auth.licensespring.com/realms/platform/broker/{company_code}/endpoint
Create, then copy:
Client ID
Client Secret
Ensure OAuth Consent Screen is configured and published.
Metadata URL
https://accounts.google.com/.well-known/openid-configuration
Microsoft Azure AD (Entra ID) — OIDC
Steps in Azure
Sign in to Azure Portal: https://portal.azure.com
Go to Microsoft Entra ID → App registrations → New registration
Important: create App registrations, not Enterprise Applications.
Enter a name (e.g., LicenseSpring OIDC)
Supported account types: Accounts in this organizational directory only
Add Redirect URI (Web): https://auth.licensespring.com/realms/platform/broker/{company_code}/endpoint
Click Register.
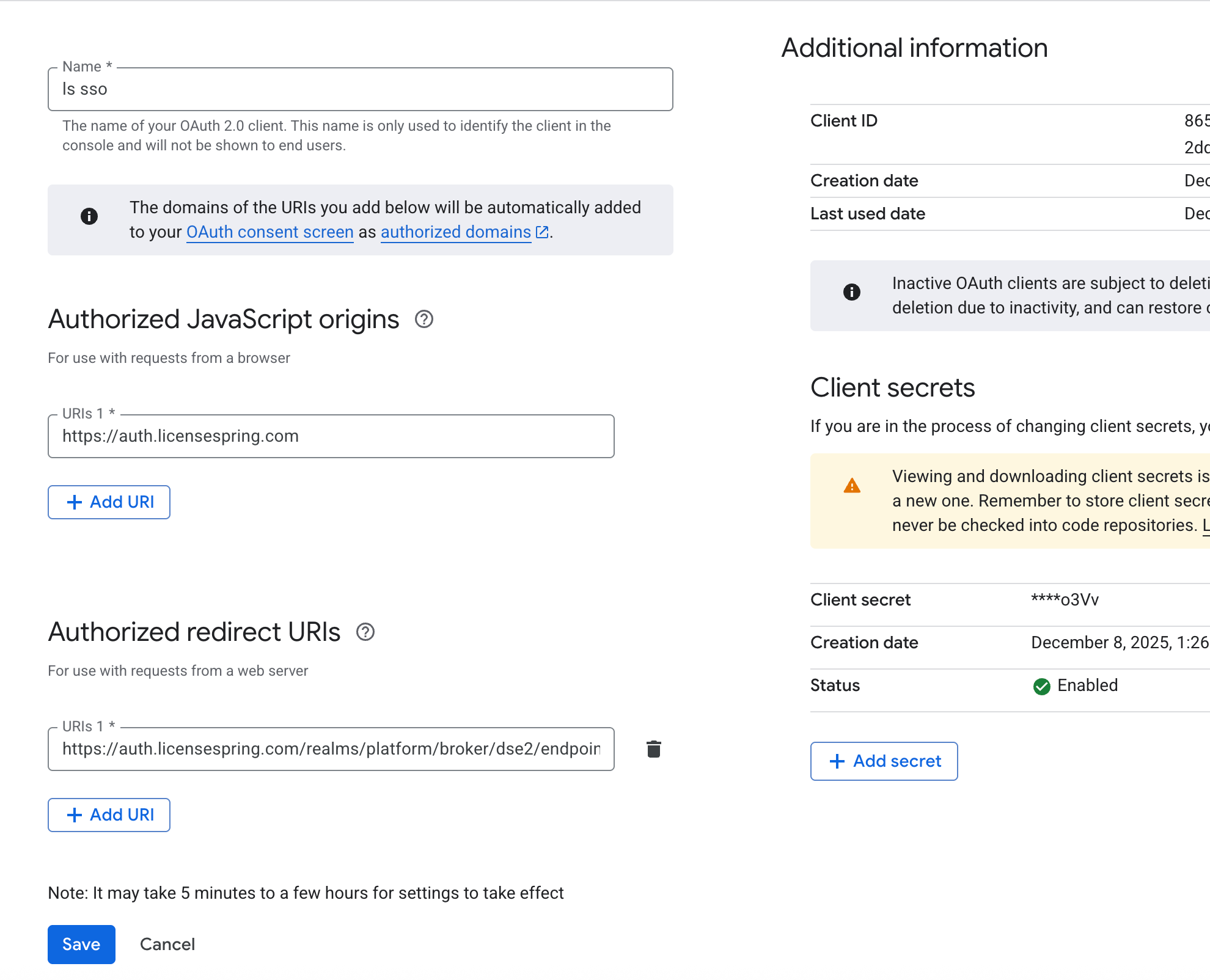
Copy Application (client) ID and Directory (tenant) ID.
Go to Certificates & secrets → New client secret. Copy the generated Client Secret Value.
Go to Authentication, confirm redirect URI is present.
(Optional) Assign users/groups to the application.
Metadata URL
https://login.microsoftonline.com/{tenant_id}/v2.0/.well-known/openid-configuration
Azure will autofill:
Authorization URL
Token URL
JWKS
Issuer
Okta (OIDC)
Steps in Okta
Log in to Okta Admin.
Applications → Create App Integration.
Sign-in method: OIDC.
Application type: Web Application.
Add Sign-in redirect URI: https://auth.licensespring.com/realms/platform/broker/{company_code}/endpoint
(Optional) Sign-out redirect URI.
Assign application to users/groups.
Copy: Okta domain, Client ID, Client Secret.
Metadata URL
https://{okta_domain}/oauth2/default/.well-known/openid-configuration
Domain example: https://dev-12345678.okta.com
Auth0 (OIDC)
Steps in Auth0
Log in: https://manage.auth0.com
Applications → Create Application → Regular Web Application
Settings → Add Allowed Callback URL: https://auth.licensespring.com/realms/platform/broker/{company_code}/endpoint
(Optional) Add same value to Allowed Logout URLs.
Copy: Domain, Client ID, Client Secret.
Save changes.
Metadata URL
https://{tenant}.auth0.com/.well-known/openid-configuration
Example: https://dev-123abc45.auth0.com
Required OIDC Information
All required metadata is in the well-known OpenID configuration which you can import, or you can fill it manually.
Configuration Steps on platform
Navigate to Platform → Settings → Single Sign-On
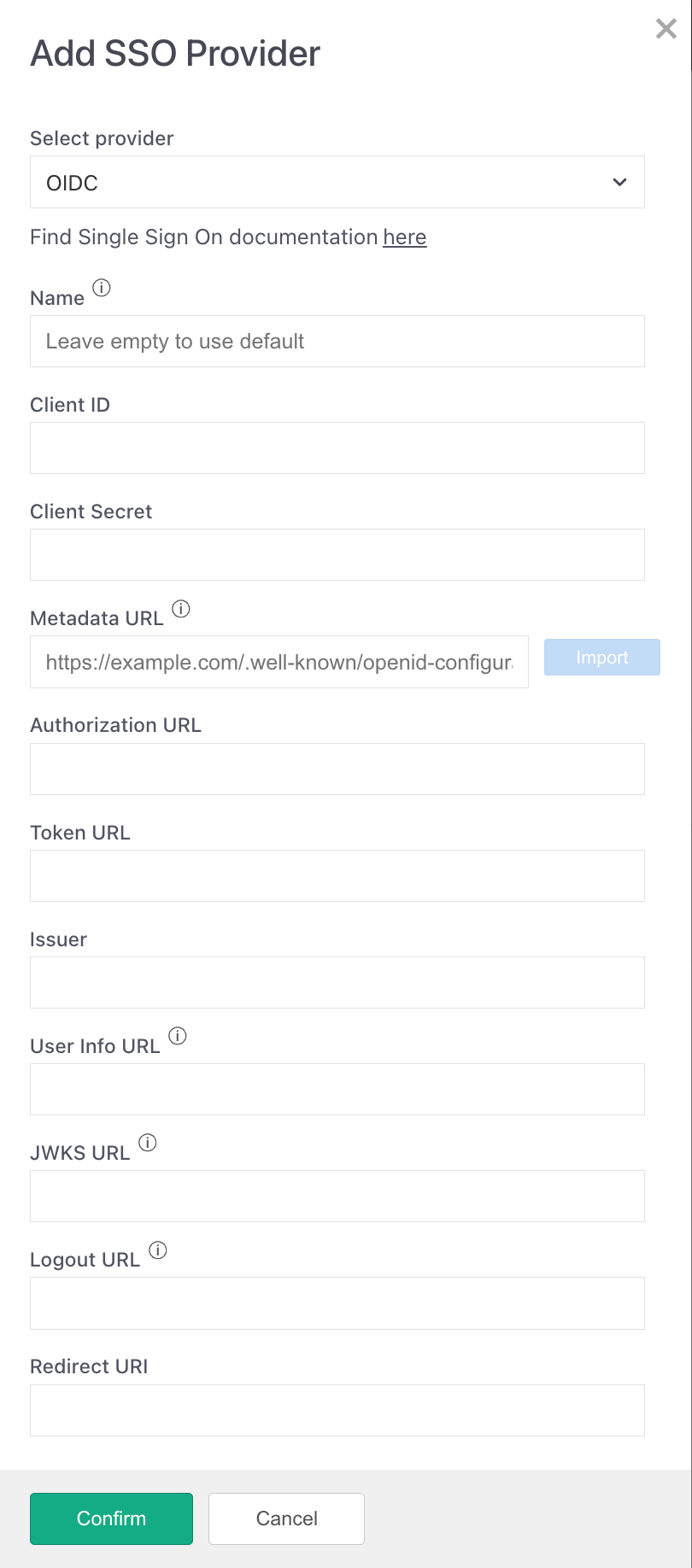
Click Add SSO Provider
Select OpenID Connect (OIDC)
Enter the required fields (Client ID, Client Secret, import well-known configuration or fill manually)
Enable (recommended): ✓ Create new platform user if it does not exist
Save the configuration
Use the SSO login on your next signin
Login Using Single Sign On
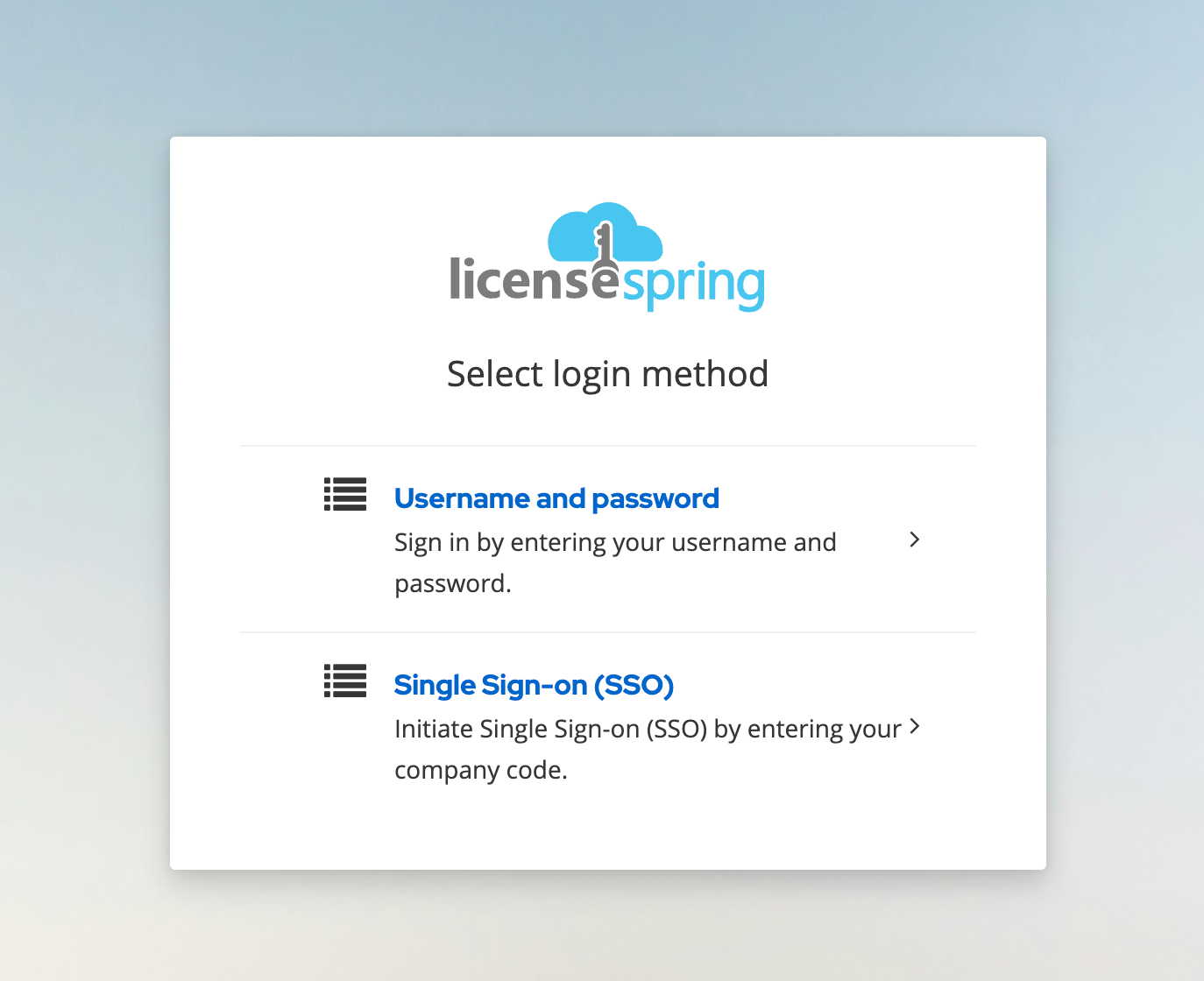
Once you have successfully added your identity provider to the LicenseSpring vendor platform SSO settings, you can log in using SSO.
Return to the LicenseSpring login page and click Change login method, then select SSO.
A prompt will ask for the company code. Enter your Company code extracted earlier.
If the provider was added correctly and there were no errors during configuration, you should be logged in to your company account.

If you require assistance or have custom SSO requirements, please contact LicenseSpring Support.
Last updated
Was this helpful?