User portal SSO
LicenseSpring supports two main end-user authentication scenarios:
User Portal SSO
The User Portal is a hosted interface provided by LicenseSpring where end users can:
View and manage their licenses
Access self-service tools (e.g., license transfers, device resets)
With SSO enabled, users can sign in to this portal using their organization’s identity provider, without needing separate LicenseSpring credentials.
License Activation via SSO
When SSO is enabled for license activation, end users authenticate with your IdP before activating a license. This ensures licenses are securely tied to verified user identities, and that only authorized users can activate or use your software.
This method is supported via the LicenseSpring SDKs and API, and is particularly useful for:
Subscription-based licensing models
User based licensing
Restricting license access to organizational members
The next section explains how to access and configure SSO settings for these scenarios within the LicenseSpring Vendor Platform.
Please note that license users SSO (Single Sign On) is only available on Enterprise plan. It allows using Single Sign On method for license activation.
Setup Single Sign On
LicenseSpring supports end-user Single Sign-On (SSO) through Customer Accounts, allowing software vendors to authenticate users within the context of a specific customer organization.
Each Customer Account can be linked to its own identity provider (IdP), enabling tailored SSO configurations for different enterprise clients. By associating SSO with Customer Accounts, LicenseSpring ensures that license access and portal authentication are securely scoped to the correct organization.
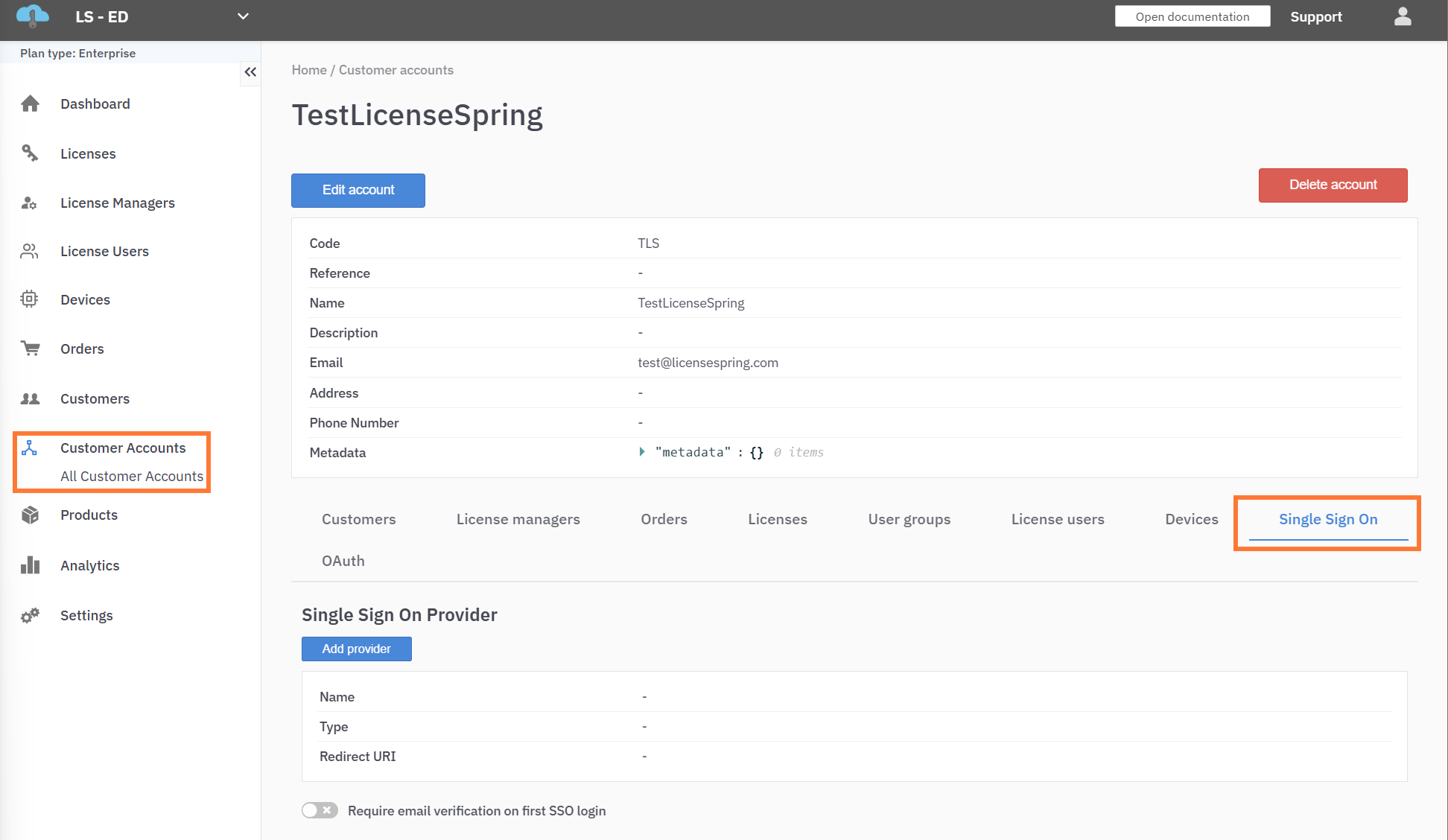
Follow the steps below to access the SSO configuration view:
Add a Provider
Click "Add Provider".
You will be prompted to enter details based on your IdP’s protocol (SAML or OIDC).
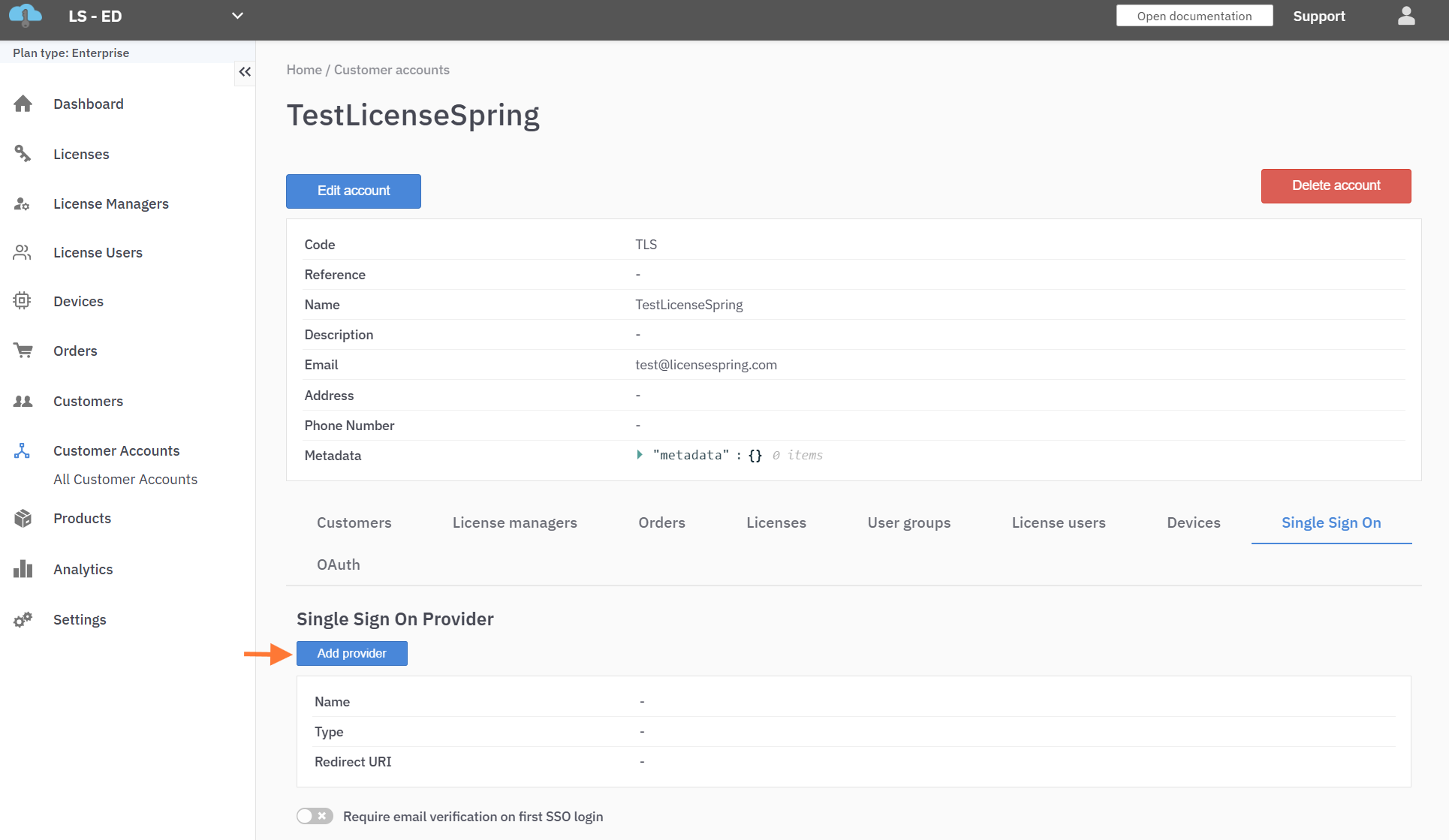
Depending on your selected Identity Provider, you will need to submit the appropriate information:
SAML: Name and .xml provider metadata file
Google: Name, Client ID, Client Secret
Apple: Service ID, Key ID, Team ID and .p8 key file
You can use only one provider at time; if you wish to switch to another, first delete the old one then follow the setup guide to add the new provider.
Account Linking and Verification
LicenseSpring automatically links accounts if the email in our system matches the email from the IdP. If no match is found, the user is presented with a login prompt to link their existing LicenseSpring account.
The settings toggle Require email verification on first SSO login can be enabled to require email verification before linking an account.
If the toggle is ON, then when you create a user they must verify their email before they can log in.
If the toggle is OFF, email verification is not required for the user to log in.
For platform users, email verification is always required due to account sensitivity.
Instructions on how to register your application to acquire required information are described below.
Redirect URI
When configuring SSO for license activation, the redirect_uri should be a local endpoint within your application that is capable of receiving and processing the authentication response from your identity provider. This URI must be registered with the IdP and securely handle the token or authorization code required to complete the sign-in and license activation flow.
With the latest SDK versions, you can configure multiple redirect URIs per application, allowing you to handle different environments while using the same SSO integration.
redirect_uri is only relevant for applications that use the SDK and allow licensed users to use SSO instead of email/password for authentication. Otherwise, everything else redirects back to the user portal.

Extracting the Company Code
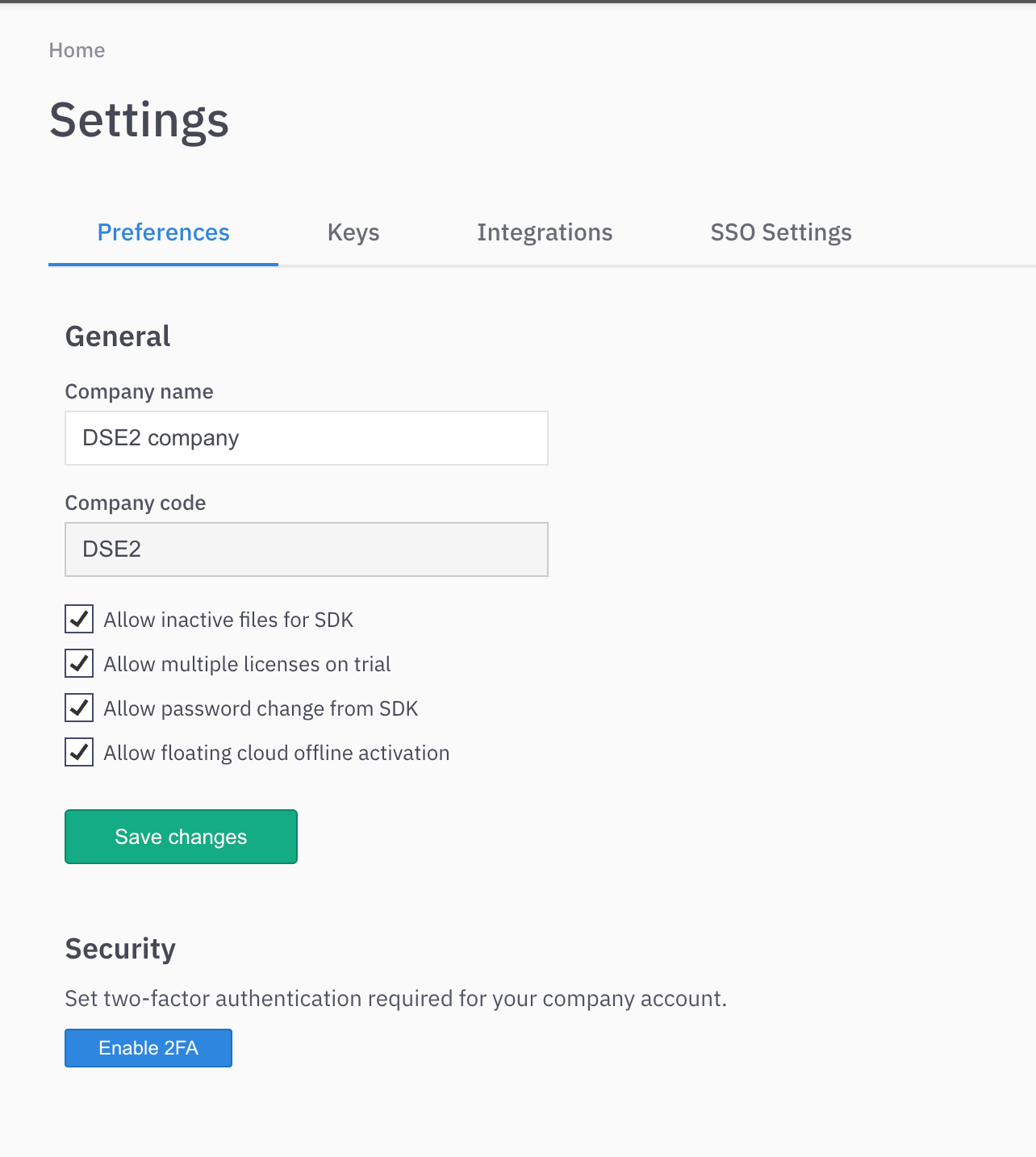
You will need the Company code to successfully register your application in your identity provider dashboard. To find your company code:
In the LicenseSpring vendor platform navigate to Settings → Preferences
Check the Company code field (example: DSE2)
Extracting the Customer Account Code
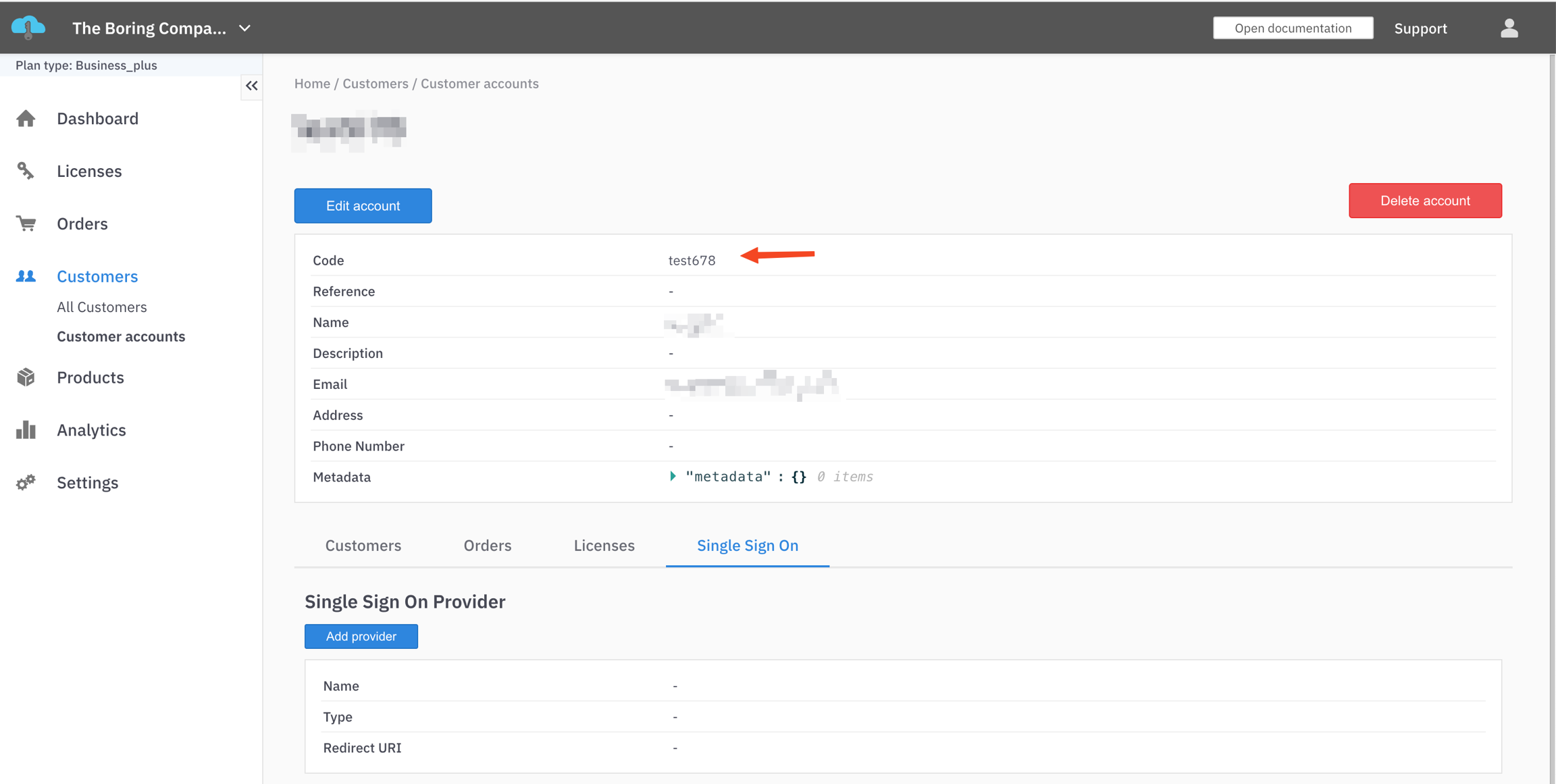
You will also need the Customer account code to register your application in your identity provider dashboard. To find the customer account code:
In the LicenseSpring vendor platform navigate to the Customer Account page for which you want to setup SSO
Check the code field (example: test678)
Integrating Social Identity Providers
Before setting up a social IdP, register your application with the respective IdP to acquire a client ID and client secret.
Google (OAuth / OIDC)
Create a Google Developer Project & OAuth Consent
Create a developer account at https://developers.google.com/identity if you haven't already.
Access the OAuth consent screen: https://console.cloud.google.com/apis/credentials/consent
Create a New Project (project dropdown → New Project). Name it and click Create.
Set Up OAuth Consent Screen:
Choose "External" and click Create.
Fill required fields like Application name and User support email.
Configure scopes (e.g., .../auth/userinfo.email, .../auth/userinfo.profile, openid).
Add test users and save.
Create OAuth 2.0 Credentials
Go to the Credentials tab, click Create Credentials → OAuth 2.0 Client ID.
Select "Web application".
Name the OAuth client (e.g., MyClient).
Add Authorized JavaScript origins: https://auth.licensespring.com (optionally users.licensespring.com).
Add Authorized redirect URI: https://auth.licensespring.com/realms/user-portal/broker/{COMPANY_CODE}-{CUSTOMER_ACCOUNT_CODE}/endpoint (example: https://auth.licensespring.com/realms/user-portal/broker/tbc-ssoacc/endpoint)
Click Create and copy Client ID and Client Secret.
Return to the Add SSO Provider form in the LicenseSpring vendor platform and complete the setup.
Apple (Sign in with Apple)
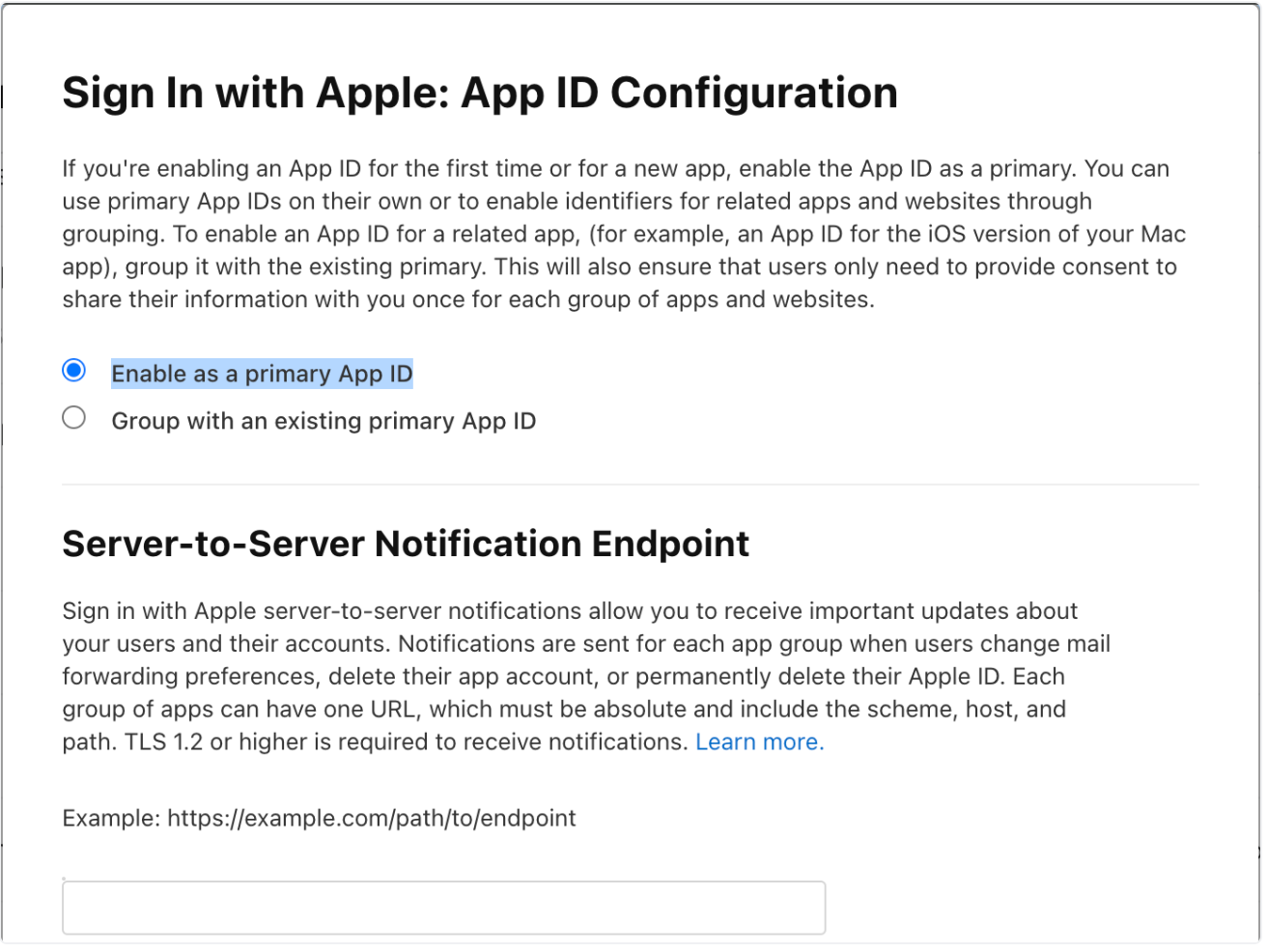
Create App ID and Enable Sign in with Apple
Navigate to Certificates, Identifiers & Profiles → Identifiers → + to create a new App ID.
Choose "App IDs", enter a description and bundle ID (e.g., keycloak).
Under Capabilities enable "Sign in with Apple".
Register and enable Sign in with Apple as needed.
Create a Service ID
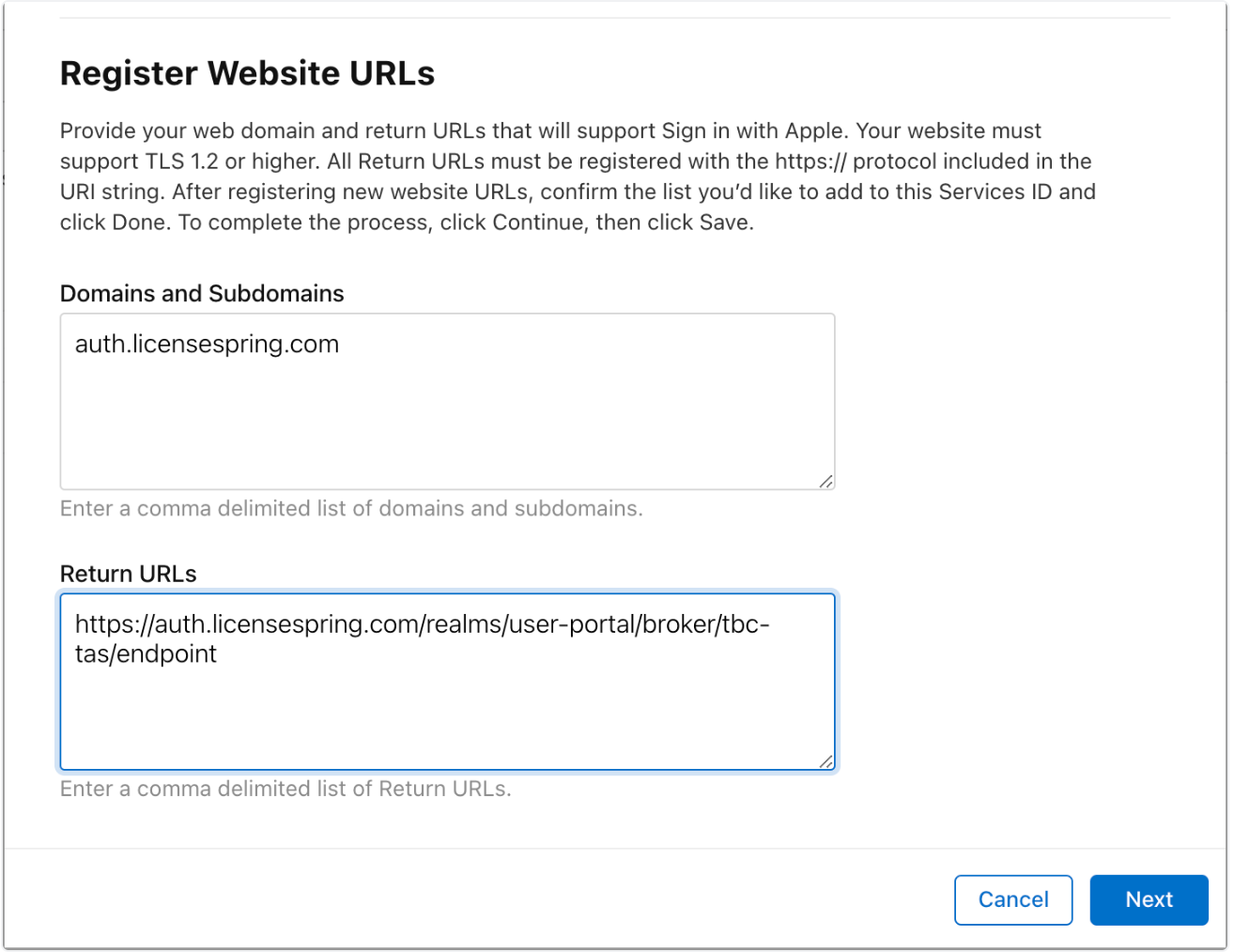
Under Identifiers → + create a new Service ID (e.g., keycloak-service).
Edit the Service ID, enable "Sign in with Apple", and configure Return URLs: https://auth.licensespring.com/realms/user-portal/broker/{COMPANY_CODE}-{CUSTOMER_ACCOUNT_CODE}/endpoint e.g. https://auth.licensespring.com/realms/user-portal/broker/tbc-tas/endpoint
Add Domains and Subdomains (without http/https): auth.licensespring.com
Add the primary App ID as the Primary App ID and click Save.
Create a Key for Apple Sign-In
Navigate to Keys → + to create a new key.
Enable "Sign in with Apple", Configure, select Primary App ID and Register.
Download the .p8 key file (you cannot download it again).
Note down your Team ID and Key ID from the developer account.
Keep the Service ID (e.g., keycloak-service) and key file ready.
Return to the Add SSO Provider form in the LicenseSpring vendor platform and finish the setup.
When you create a new App ID, it may take up to a few hours for changes to apply.
Incorporating SAML Identity Providers
Azure Active Directory (SAML)
Configure Basic SAML Settings
Edit Basic SAML Configuration:
Identifier (Entity ID): https://auth.licensespring.com/realms/user-portal
Reply URL (Assertion Consumer Service URL): https://auth.licensespring.com/realms/user-portal/broker/{COMPANY_CODE}-{CUSTOMER_ACCOUNT_CODE}/endpoint e.g. https://auth.licensespring.com/realms/user-portal/broker/tbc-tas/endpoint
Save and close.
Set Attributes & Claims
Ensure Unique User Identifier (Name ID) is set to user.mail.
We use email as the NameID. If UserPrincipalName (UPN) is not the user’s primary email in the platform, update it accordingly (important when users have multiple aliases).
Download Federation Metadata XML and provide the provider name and the downloaded metadata (.xml) in the Add SSO Provider form.
Common Azure provider SSO errors can occur if users are not assigned to the app. See steps below to resolve.
To resolve the common Azure SSO error:
In the Azure Active Directory Admin Center, select your app, then choose the application to which you want to assign the user account.
In the left pane select Users and Groups and then select Add User/Group.
On the Add Assignment pane, click None Selected under Users and Groups, search for and select the user to assign, then click Select.
On the Add Assignment pane, select Assign at the bottom.
After completing these steps the user should be able to sign in using SSO.
For SAML we use the Name ID format emailaddress.
Upload the downloaded .xml file by choosing SAML for AuthO and confirm to add it. Return to Add SSO Provider in the LicenseSpring platform and finish the setup.
Auth0 (SAML)
Configure SAML Addon
Applications → select your app → Addons tab → activate SAML2 Web App.
In Addon Settings:
Application Callback URL: https://auth.licensespring.com/realms/user-portal/broker/{COMPANY_CODE}-{CUSTOMER_ACCOUNT_CODE}/endpoint
For minimal settings configure email as the NameID with the following (example) JSON:
Optionally Debug by logging in as the test user.
Enable and Save the addon.
On the Usage tab download the Identity Provider Metadata (.xml).
Return to Add SSO Provider in the LicenseSpring platform and finish the setup.
Okta (SAML)
Configure SAML Settings
Single sign on URL: https://auth.licensespring.com/realms/user-portal/broker/{COMPANY_CODE}-{CUSTOMER_ACCOUNT_CODE}/endpoint e.g. https://auth.licensespring.com/realms/user-portal/broker/tbc-tas/endpoint
Audience URI (SP Entity ID): https://auth.licensespring.com/realms/user-portal/broker/{COMPANY_CODE}-{CUSTOMER_ACCOUNT_CODE}/endpoint
Ensure NameID Format is EmailAddress (General tab).
Leave other defaults or adjust as needed → Next → Finish.
Assign Users and Get IdP Metadata
Assign users under the Assignments tab → Assign to People → select user → Save.
On the Sign On tab find Identity Provider metadata. Right-click and copy the URL or use "View SAML setup instructions" to save the IDP metadata into an .xml file.
Upload the .xml file in the Add SSO Provider form and complete the setup.
For SAML we use the Name ID format emailaddress.
OpenID Connect (OIDC) Integration
LicenseSpring supports SSO via OpenID Connect (OIDC). Customers may integrate any IdP that supports the Authorization Code Flow, including:
Azure Active Directory (Entra ID)
Okta
Auth0
Google Identity
This allows organizations to authenticate users with their own identity system while LicenseSpring handles user provisioning and access control.
OIDC Redirect URI
Every OIDC provider must be configured to redirect authentication responses to the following URL:
https://auth.licensespring.com/realms/user-portal/broker/{company_code}-{customer_account_code}/endpoint
Replace {company_code} with the company code assigned to your organization in LicenseSpring. This redirect URI must match exactly in your identity provider configuration.
Google Identity (OIDC)
Steps summary:
Go to https://console.cloud.google.com
APIs & Services → Credentials → Create Credentials → OAuth client ID
Application type: Web Application
Authorized JavaScript origins: https://auth.licensespring.com
Authorized redirect URI: https://auth.licensespring.com/realms/user-portal/broker/{company_code}-{customer_account_code}/endpoint
Create and copy Client ID and Client Secret
Ensure OAuth Consent Screen is configured and published
Metadata URL: https://accounts.google.com/.well-known/openid-configuration
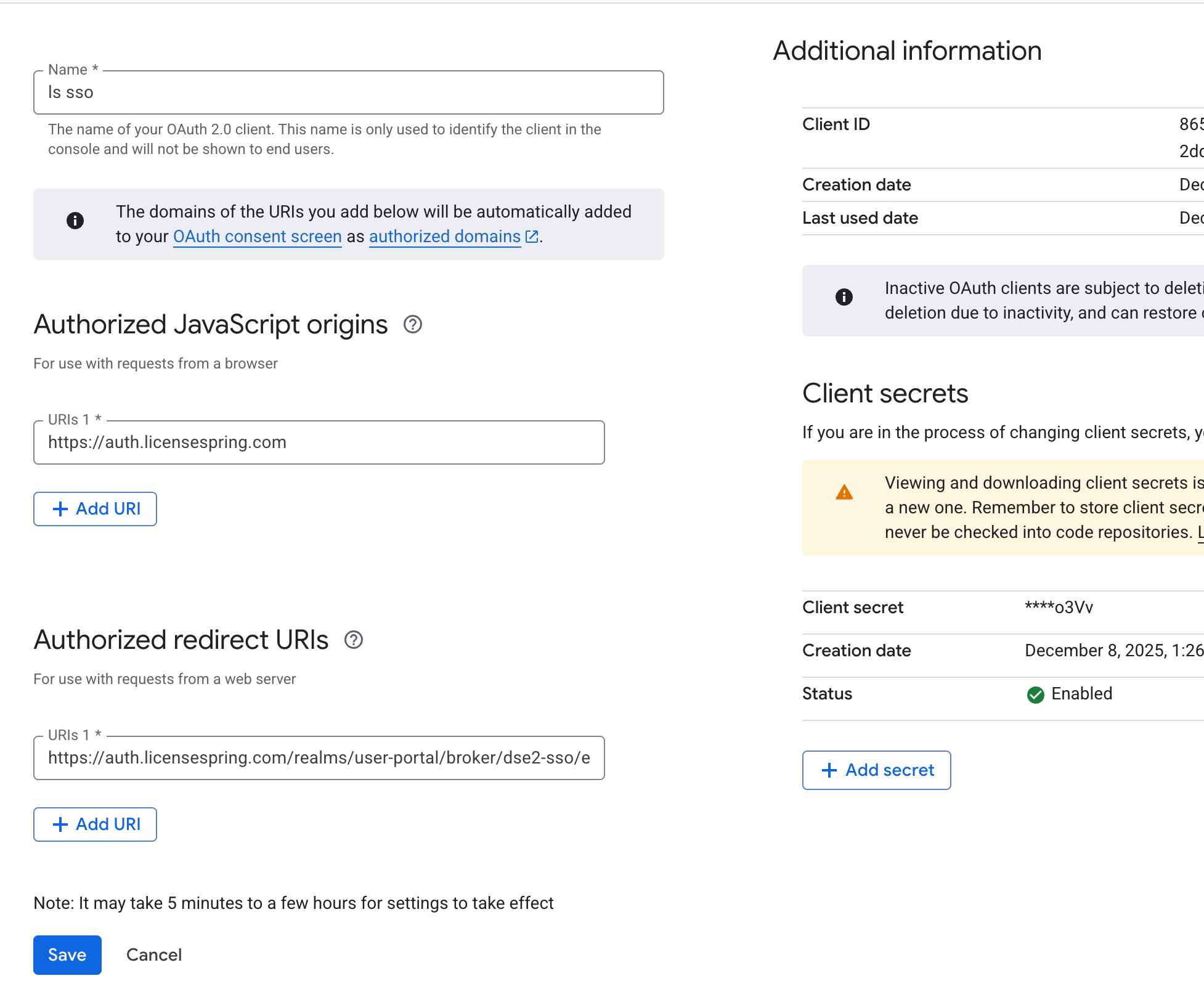
Microsoft Azure AD (Entra ID) — OIDC
Steps summary:
Azure Portal: https://portal.azure.com
Microsoft Entra ID → App registrations → New registration
Important: create App registrations (not Enterprise Application)
Enter a name (e.g., LicenseSpring OIDC)
Supported account types: Accounts in this organizational directory only
Add Redirect URI (Web): https://auth.licensespring.com/realms/user-portal/broker/{company_code}-{customer_account_code}/endpoint
Register and copy Application (client) ID and Directory (tenant) ID
Certificates & secrets → New client secret → copy the Client Secret Value
Confirm redirect URI under Authentication
(Optional) Assign users/groups to the application
Metadata URL: https://login.microsoftonline.com/{tenant_id}/v2.0/.well-known/openid-configuration
Azure will autofill Authorization URL, Token URL, JWKS, Issuer.
Okta (OIDC)
Steps summary:
Log in to Okta Admin
Applications → Create App Integration
Sign-in method: OIDC, Application type: Web Application
Add Sign-in redirect URI: https://auth.licensespring.com/realms/user-portal/broker/{company_code}-{customer_account_code}/endpoint
(Optional) Sign-out redirect URI
Assign application to users/groups
Copy Okta domain, Client ID, Client Secret
Metadata URL: https://{okta_domain}/oauth2/default/.well-known/openid-configuration
Example domain: https://dev-12345678.okta.com
Auth0 (OIDC)
Steps summary:
Log in: https://manage.auth0.com
Applications → Create Application → Regular Web Application
Settings → Allowed Callback URLs: https://auth.licensespring.com/realms/user-portal/broker/{company_code}-{customer_account_code}/endpoint
(Optional) Add Allowed Logout URLs
Copy Domain, Client ID, Client Secret
Save changes
Metadata URL: https://{tenant}.auth0.com/.well-known/openid-configuration Example tenant: https://dev-123abc45.auth0.com
Required OIDC Information
All required metadata is available in the well-known OpenID configuration (/.well-known/openid-configuration) which you can import, or you can fill manually if needed.
Configuration Steps on Platform
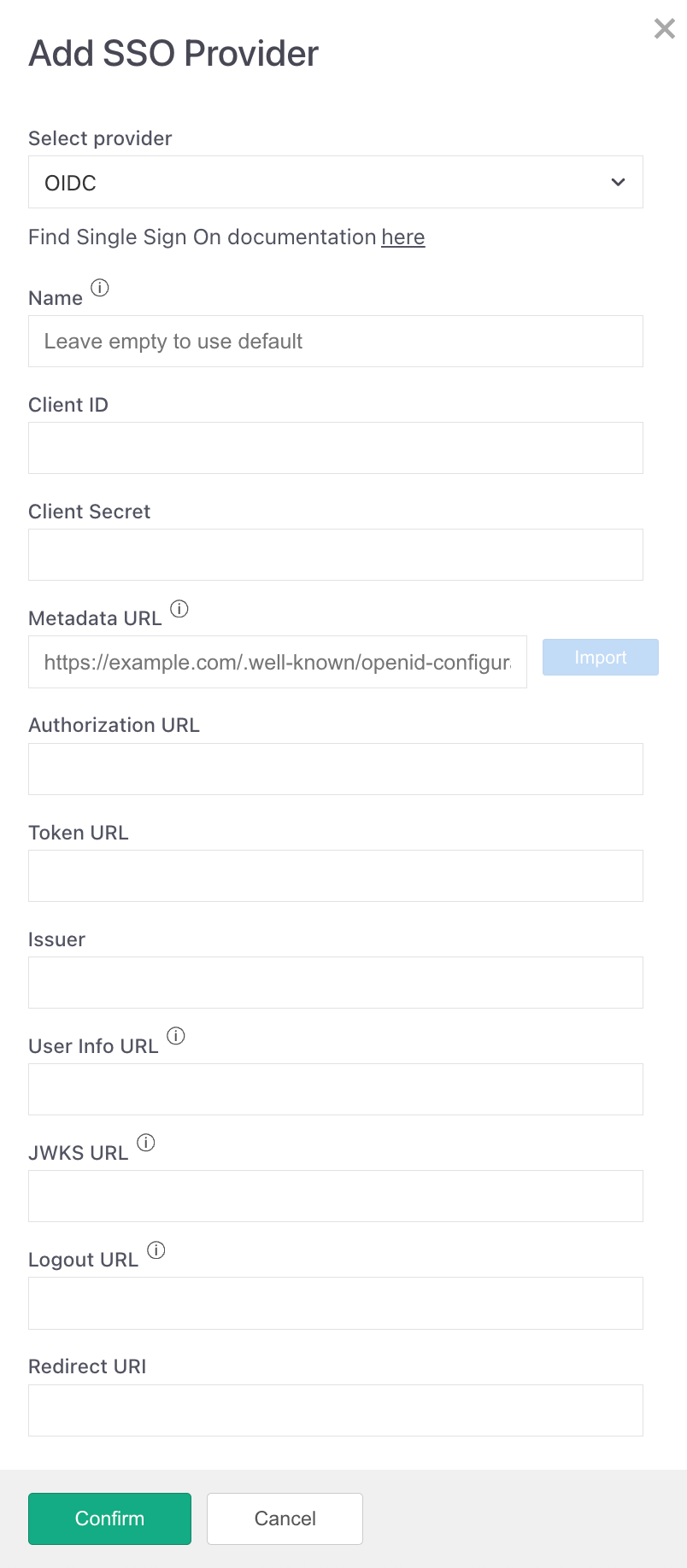
Navigate to Platform → Settings → Customer Accounts → Single Sign-On and then:
Click Add SSO Provider
Select OpenID Connect (OIDC)
Enter required fields (Client ID, Client Secret, import well-known configuration or enter manually)
Enable (recommended): ✓ Create new platform user if it does not exist
Save the configuration
Use the SSO login on your next sign-in
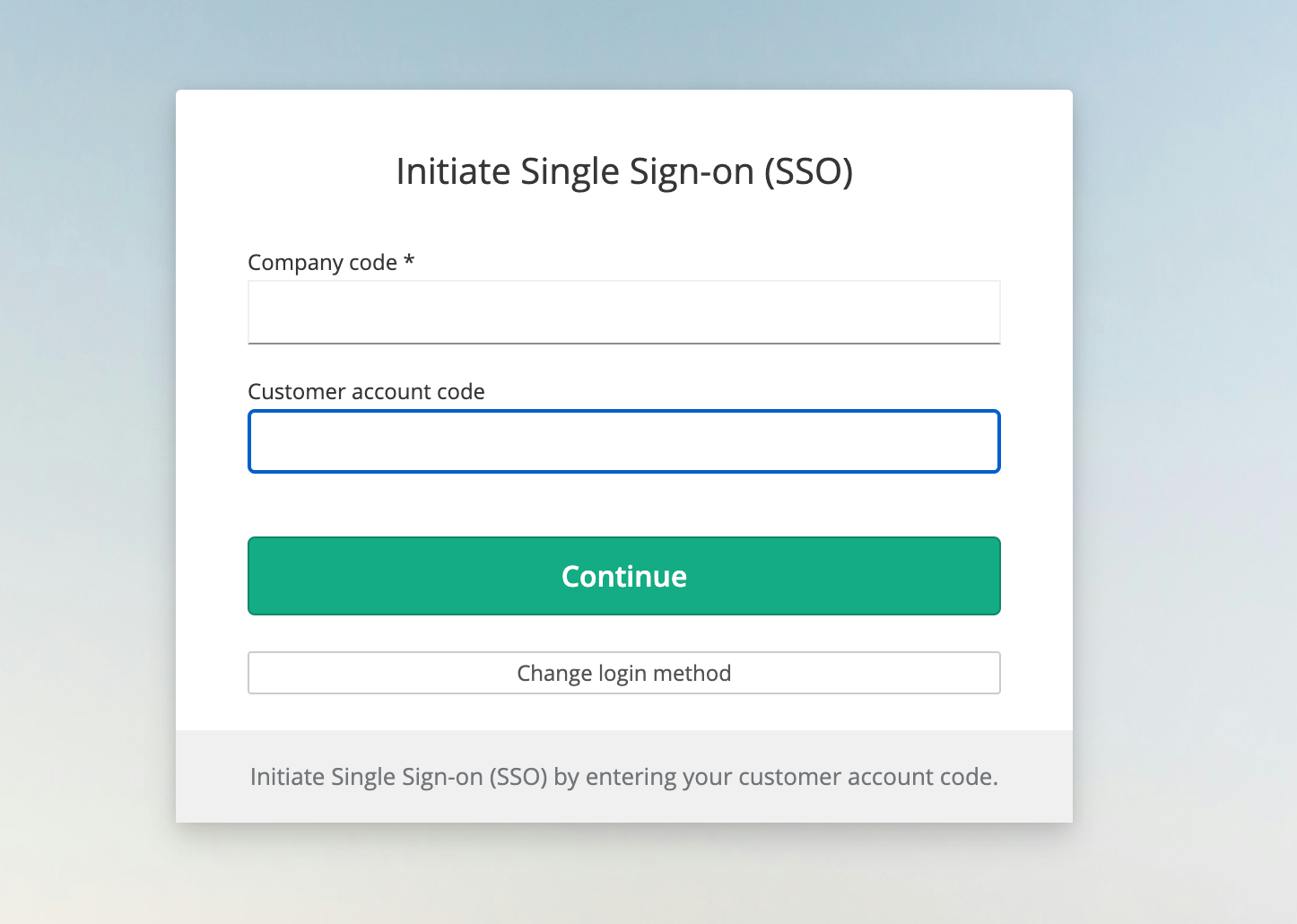
Login to the User Portal using SSO
Once you have added your identity provider to the customer account SSO settings, every license user and license manager assigned to this customer account can log in to the user portal.
User portal URL: https://users.licensespring.com
The SSO login process is the same as for the vendor platform SSO. On the login screen click the Change Login Method button and select Single Sign-on (SSO). A prompt will ask for the customer account code and company code — enter the codes you extracted in previous steps.
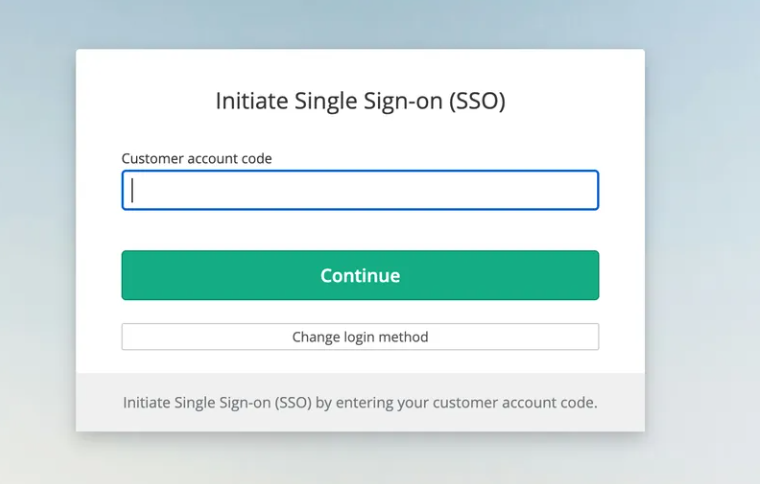
User portal subdomains for Enterprise accounts
For Enterprise accounts, we host the user portal on a company-code subdomain. This removes the requirement for users to input their company code during login.
Access via: https://{company_code}.users.licensespring.com
By navigating to the custom subdomain (e.g., https://company_code.users.licensespring.com), users are automatically linked to their respective customer accounts and do not need to input customer code.
License API Authentication
If you plan to use the License API directly to authenticate users using Single Sign-on instead of username/password, follow these steps.
Get Single Sign On Hosted UI URL
The /api/v4/sso_url endpoint returns the URL where the hosted login UI is served. To create the correct URL you need to use:
customer_account_code of the customer account for which the user pool and providers have been created
product_short_code of the product defined in LicenseSpring
Details for this endpoint are written in the Single Sign-On URL page. Use the URL from the response to open the hosted UI through which your users can login. Details for this endpoint are written in Single Sign On URL. Use the URL from the response to open the hosted UI through which your users can log in.
Extract the id_token or code from the redirect_url and Activate the License
After successful login on the hosted UI, users will be redirected to the URL from redirect_uri. The response will include query parameters such as id_token or code (if using Authorization Code Grant).
Along with the customer_account_code, send this value to the Activate License (Online Method) endpoint. The license user needs to be assigned to the license being activated.
Our SDKs support SSO license activation natively. See Single Sign On.
If you require assistance or have custom SSO requirements, please contact LicenseSpring Support.
Last updated
Was this helpful?