Configuration & Provisioning
Create the Configuration File
1
2
3
database:
# if using sqlite
type: sqlite
path: ./data/db.sqlite
# if using sqlcipher
type: sqlcipher # <-- switch from sqlite to sqlcipher
path: ./data/app.db
password: "your-password"
# if using postgres
type: postgres
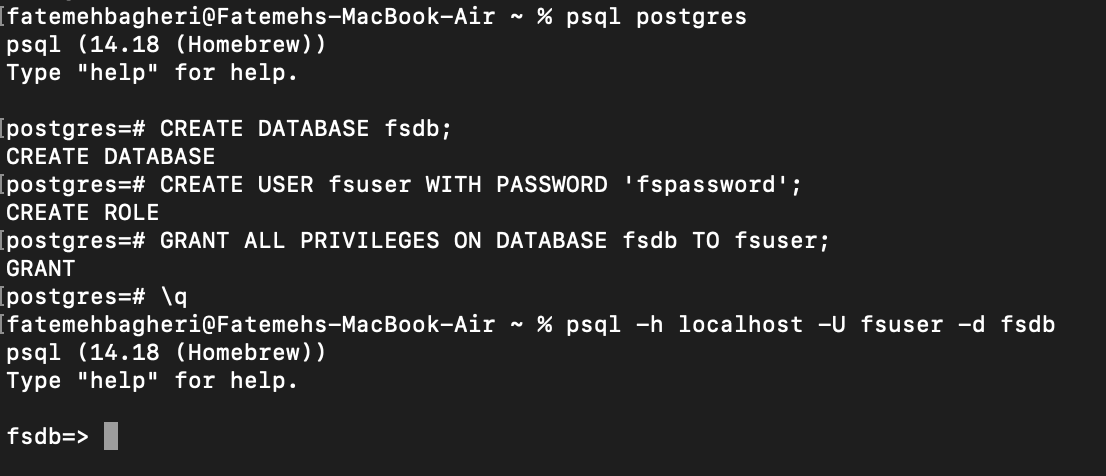
host: localhost
port: 5432
user: fsuser
password: fspassword
name: fsdb
sslmode: "disable" # options: disable, require, verify-ca
sslrootcert: "/path/to/sslcert/ca.crt" # ignore if sslmode: "disable"
CryptoProviderKey: "" # secret used to encrypt db data in OAuth mode
server:
port: 8080 # port on which the server runs
Verbose: true # level of information given in logs
BasePath: "" # path prefix of the server
DisableUserAuth: false # disable user authentication requirement, not admin!
cloud:
UseOAuth: false
# if authenticating with API/Shared key
APIKey: ""
SharedKey: ""
# if authenticating with OAuth
ClientId: ""
ClientSecret: ""
# cloud server config
BaseURL: "" # default: "https://api.licensespring.com"
APIPrefix: "" # default: "/api/v4/"
ServerPublicKey: "" # default: LicenseSpring Prod's public key
# if having Airgap licenses, fetch this key from platform
AirgapPublicKey: ""
# provisioning config
UseHardwareKey: false # choose provisioning method
HardwareKeyPIN: "" # optional, custom PIN
PrivateKeyPath: "" # path to generated priv key. Ignore if using hardware key
CertificatePath: "" # path to cert received from LSDatabase Configuration
SQLite
SQLCipher Integration
Installing SQLCipher
PostgreSQL
CryptoProviderKey
Server Configuration
Cloud Configuration
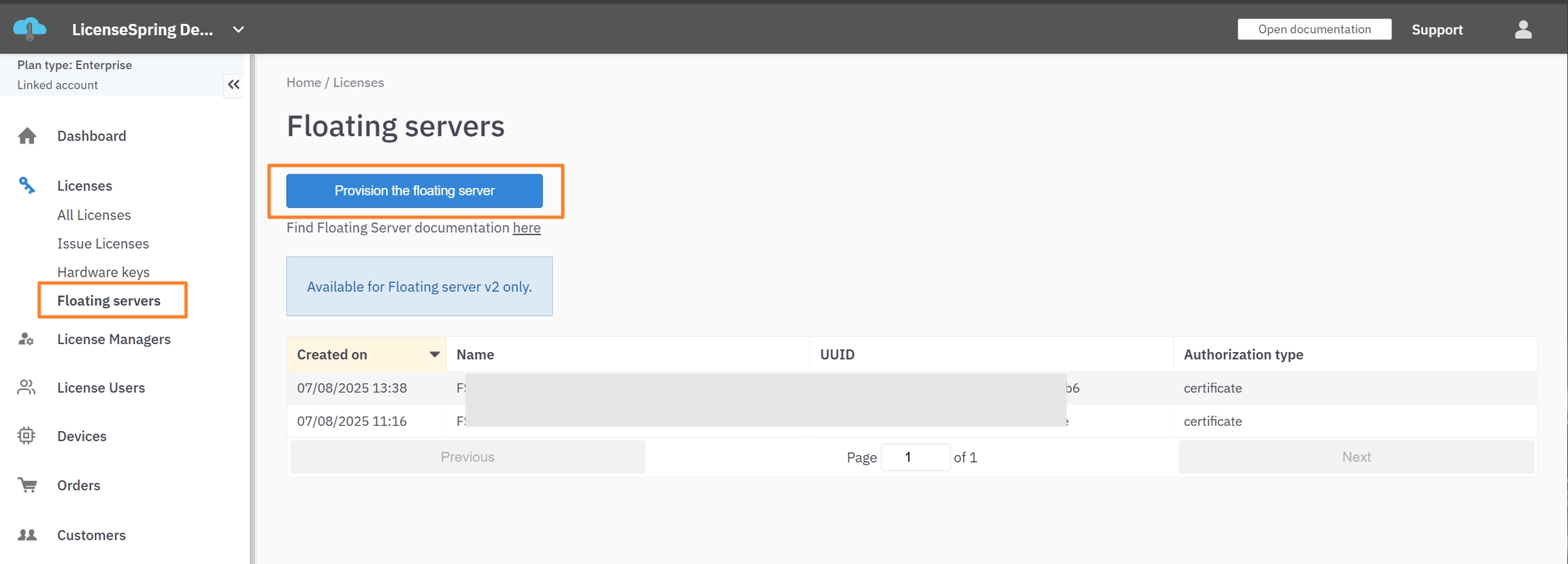
Provisioning the Floating Server
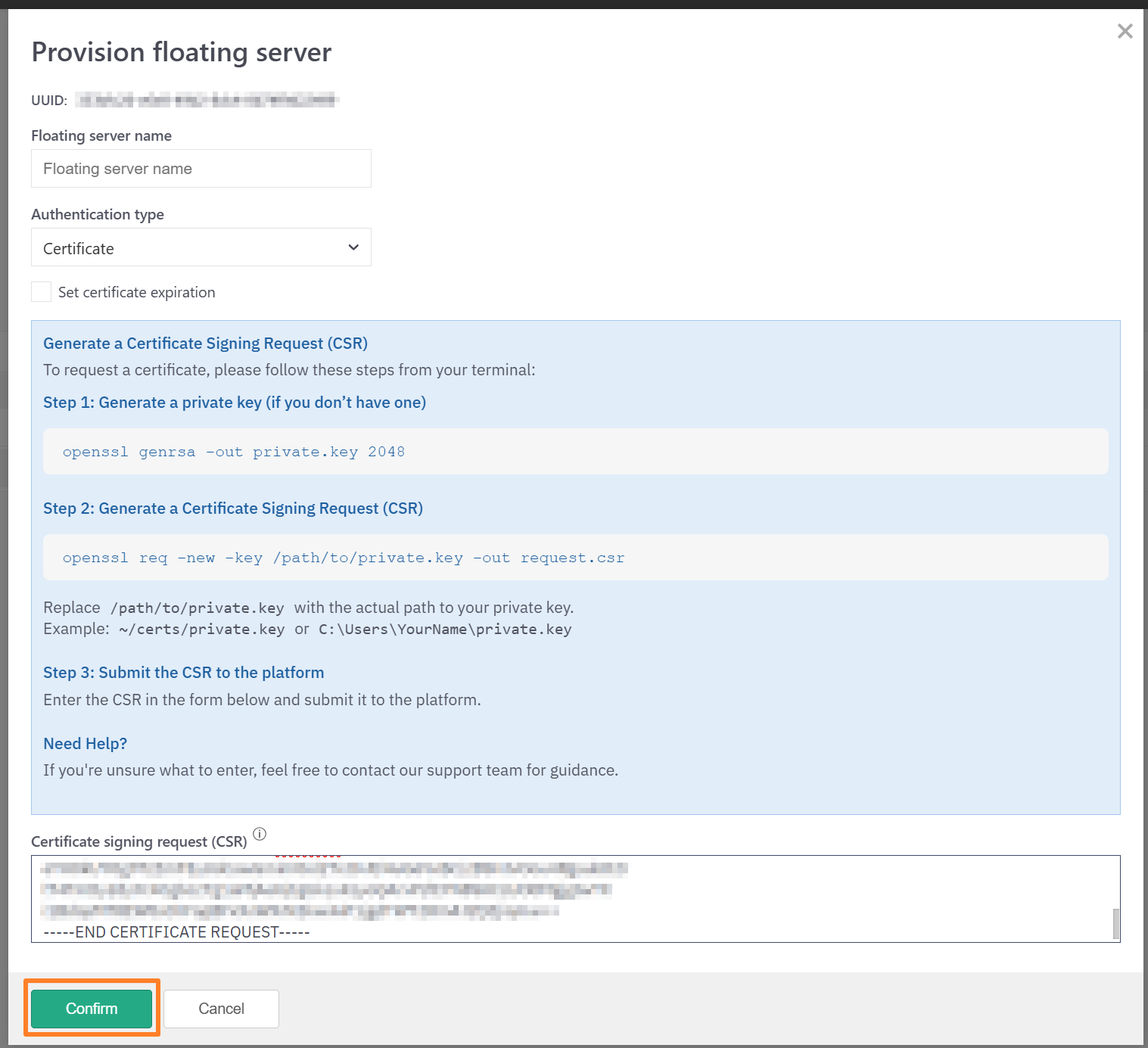
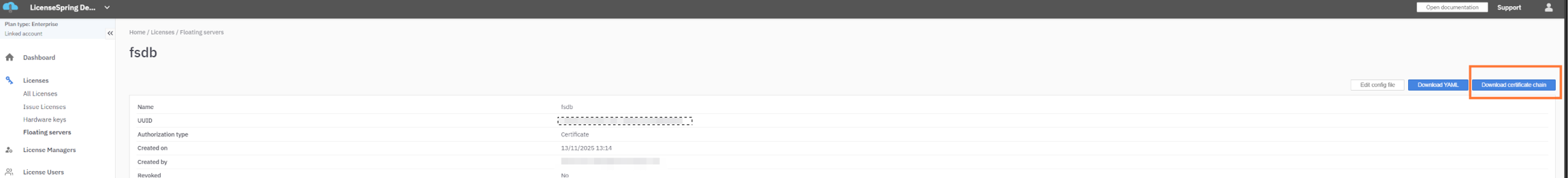
Floating Server Provisioning with Certificates (CSR)
Floating Server Provisioning Using a Hardware Key
Optional: Set a Custom Hardware Key PIN
Configuration for Hardware Key Provisioning
Requirements
1
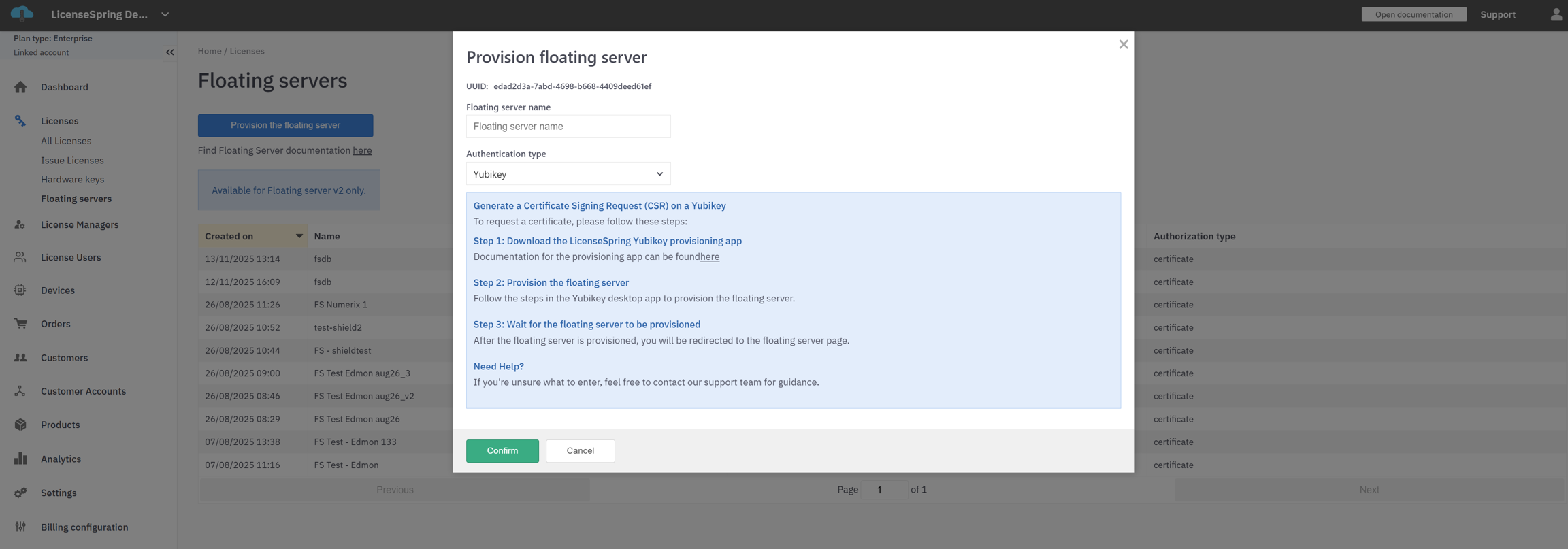
Create a License for Hardware Key–Based Floating Server Use
1
2
3
4
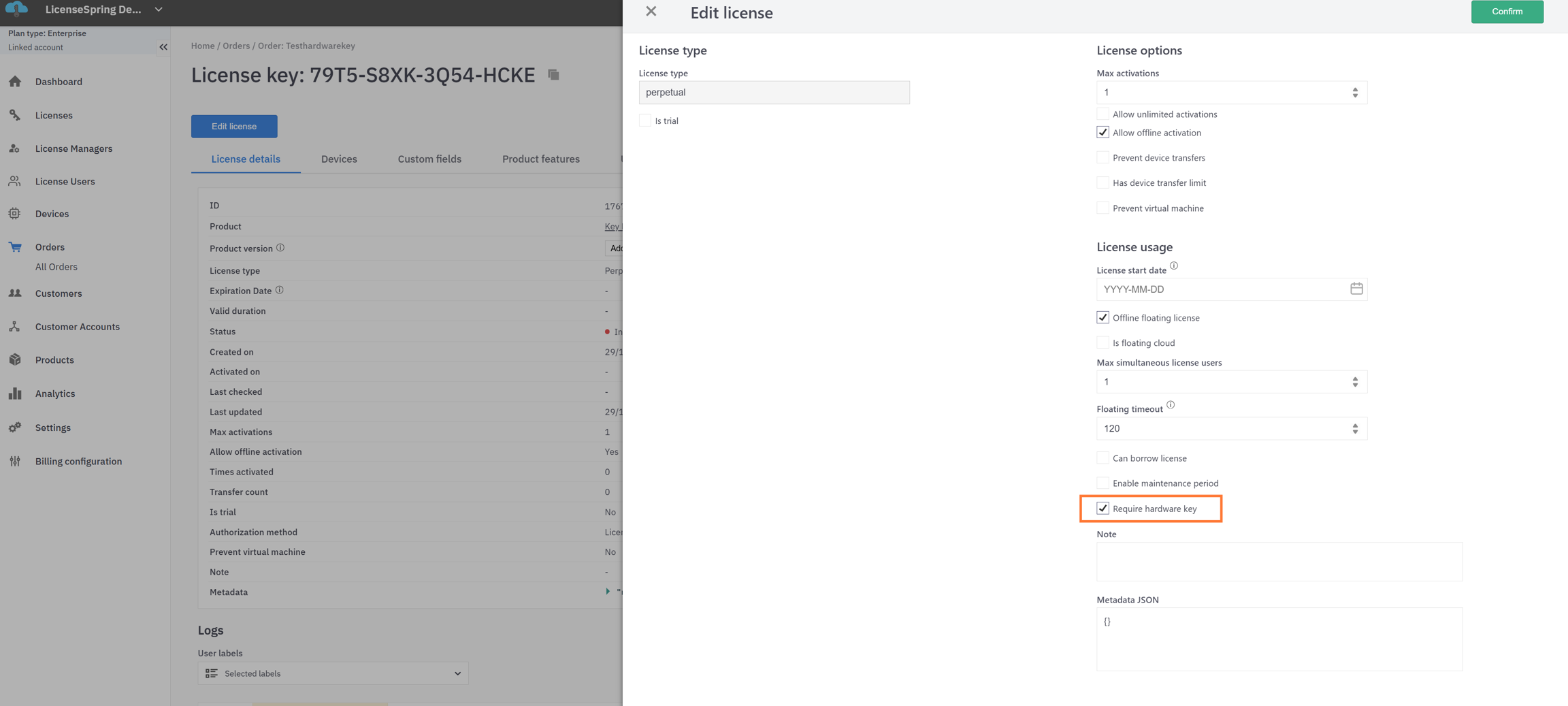
Hardware Key and Server Lifecycle
Last updated
Was this helpful?